- Solutions
INTEGRATIONS
Integrate with any data source, notify any service, authenticate your way, and automate everything.
- Products
Apica Product Overview
Apica helps you simplify telemetry data management and control observability costs.FleetFleet Management transforms the traditional, static method of telemetry into a dynamic, flexible system tailored to your unique operational needs. It offers a nuanced approach to observability data collection, emphasizing efficiency and adaptability.Flow100% pipeline control to maximize data value while reducing observability spend by 40%. Collect, optimize, store, transform, route, and replay your observability data — however, whenever, and wherever you need it.LakeApica’s data lake (powered by InstaStore™), a patented single-tier storage platform that seamlessly integrates with any object storage. It fully indexes incoming data, providing uniform, on-demand, and real-time access to all information.ObserveThe most comprehensive and user-friendly platform in the industry. Gain real-time insights into every layer of your infrastructure with automatic anomaly detection and root cause analysis.Synthetic MonitoringUnlock the power of synthetic monitoring with Apica. Tailored for enterprises, our robust monitoring tool delivers predictive insights into the performance and uptime of your critical assets – websites, applications, APIs, and IoT.Test Data OrchestratorApica Test Data Orchestrator (TDO) transforms test data management with self-service automation and AI-driven intelligence, eliminating delays and enabling teams to provision right-sized, compliant test data on demand. - Resources
Videos
Dive into valuable discussions and get to know our company through exclusive video content.Events & Webinars
Join us for live and virtual events featuring expert insights, customer stories, and partner connections. Don’t miss out on valuable learning opportunities!
DOCUMENTATION
Find easy-to-follow documentation with detailed guides and support to help you use our products effectively. - Company
About Us
Apica keeps enterprises operating. The Ascent platform delivers intelligent data management to quickly find and resolve complex digital performance issues before they negatively impact the bottom line.Security
In a world in constant motion where threat actors are everywhere it is important to always improve the security in all parts of your organization. We believe that is done by leveraging industry best practices and adopting the latest technology. We are proud to be both ISO27001 and SOC2 certified and thus your data is safe and secure with us.News
Stay updated with the latest news and press releases, featuring key developments and industry insights.
Leadership
Meet our leadership team, dedicated to driving innovation and success. Discover the visionaries behind our company’s growth and strategic direction.Apica Partner Network
Join the Apica Partner Network and collaborate with industry leaders to deliver cutting-edge solutions. Together, we drive innovation, growth, and success for our clients.Careers
Build your future with us! Explore exciting career opportunities in a dynamic environment that values innovation, teamwork, and professional growth. - Login
Get Started Free
Get Enterprise-Grade Data Management Without the Enterprise Price Tag Manage Your Data Smarter – Start for FreeLoad Test Portal
Ensure seamless performance with robust load testing on Apica’s Test Portal powered by InstaStore™. Optimize reliability and scalability with real-time insights.
Monitoring Portal
Access the Monitoring Portal (powered by InstaStore™) to view live system performance data, monitor key metrics, and quickly identify any issues to maintain optimal reliability and uptime.
HIDS
Fortify Your Systems.
Detect Stealthy Threats.
Master Security Management.
proactively protect your systems by detecting intrusions, monitoring file integrity, analyzing logs, and unmasking rootkits. Enforces policy compliance, detect anomalies, and centralize management for informed decision-making and a robust security posture.
problem
Are you struggling to handle
vast data from complex, distributed systems efficiently?

Undetected intrusions and breaches

Unauthorized file
changes
Inefficient analytics and overlooked threats

Hidden rootkits compromising security

Unidentified
malware infections

Inconsistent
policy enforcement

Overlooked anomalies and delayed alerts

Decentralized security management
BENEFITS
We Can Help.
See How.
Intrusion detection and prevention
File integrity
monitoring
monitoring
Log analysis and monitoring
Rootkit
detection
detection
Malware
detection
detection
Policy enforcement and compliance
Anomaly detection and alerting
Centralized management and reporting
FEATURES
Every control.
At your fingertips.
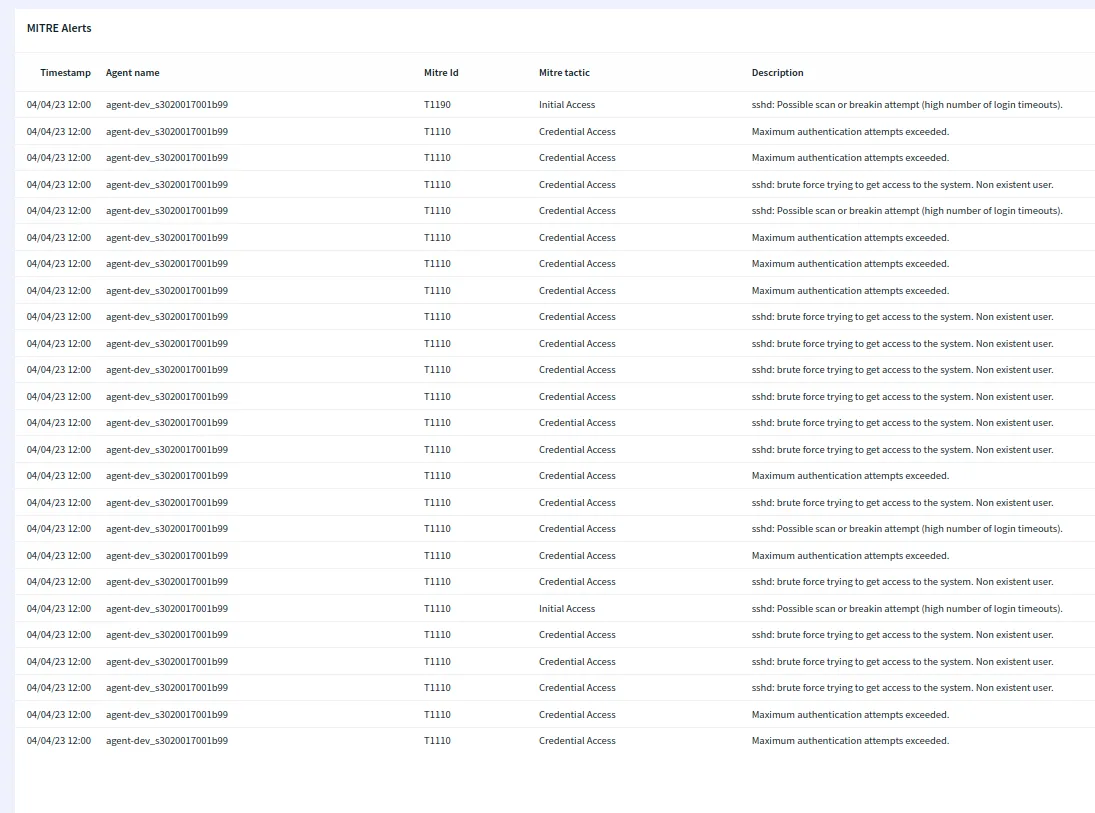
Intrusion detection and prevention
Actively safeguards your systems from unauthorized access, enhancing security and minimizing the risk of data breaches.
File integrity monitoring
Detects unauthorized file modifications, ensuring data integrity and helping prevent potential security threats.

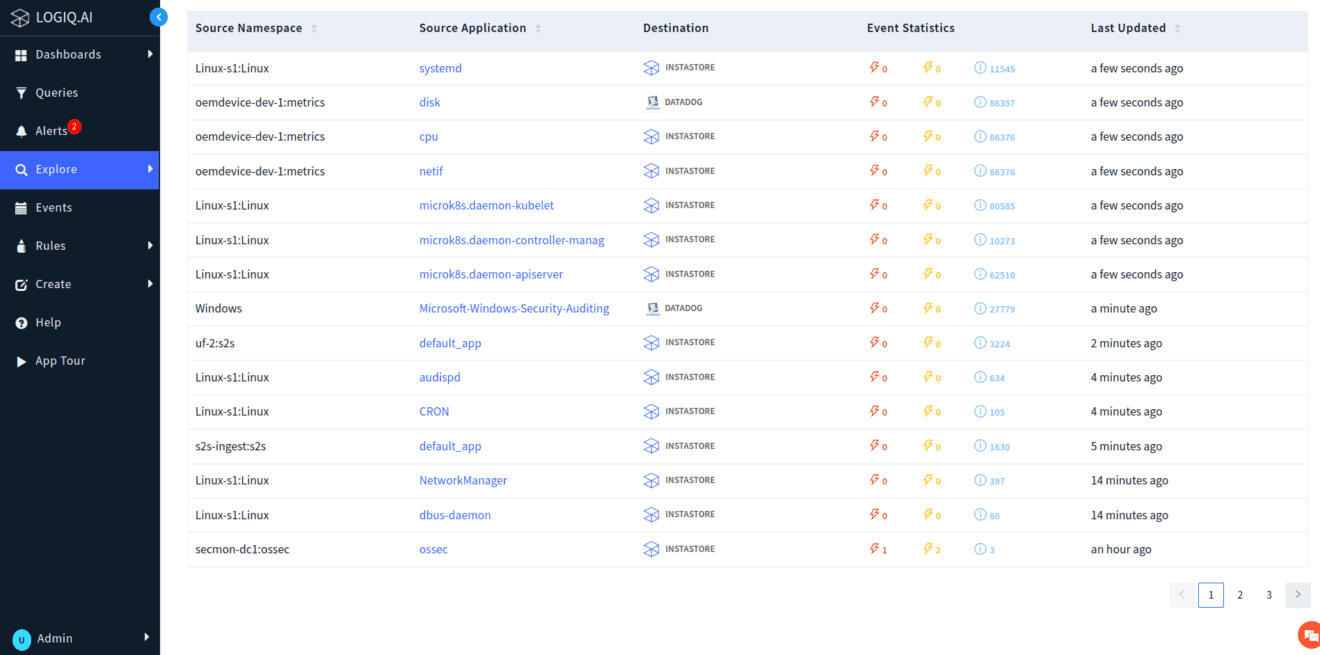
Log analysis and monitoring
Streamlines log management and identifies critical events, enabling timely responses and informed decision-making.
Rootkit detection
Unveils hidden rootkits, bolstering system security and thwarting covert threats.

Get our Comprehensive Logs Data Sheet right into your Inbox
More Features
Malware detection
Identifies and isolates malicious software, protecting critical data and system performance.
Policy enforcement and compliance
Ensures consistent adherence to security policies and regulatory standards, mitigating the risk of penalties and reputational damage.
Anomaly detection and alerting
Pinpoints unusual behavior, facilitating rapid response to potential security issues and minimizing potential damage.
Centralized management and reporting
Simplifies security administration and delivers comprehensive insights, empowering informed, data-driven decision-making.
INTEGRATE WITH ANY STACK



*Trademarks belong to the respective owners.
PRICING
Reclaim control of data, cost and complexity.
^Free Plan is available only for self-hosting and is supported under the Basic Support plan.
* SaaS prices are for annual contracts. Save 25-40% on annual contracts compared to pay-as-you-go rates.
Self-hosted deployments are available only on annual plans.
SECURE
Edge
Protection
Secure your enterprise with powerful extended security.
| Free Plan^ | Upto 20 Hosts |
| Self-hosted | $5/Host/mo |
| SaaS | $5/Host/mo* |
- Host intrusion detection (HIDS).
- SIEM and SOAR.
- Multi-petabyte scale.
